Follow the Crypto Part 2: Tools and Techniques for Investigating Cryptocurrency Transactions

In part one of our “Follow the Crypto” series, we highlighted the growing need for cryptocurrency investigations in the fight against fraud. We discussed the hurdles that investigations face, from the anonymous nature of transactions to the complexity of analyzing blockchain data, but also noted some famous successful investigations.
In this second and final part, we will delve into the ‘how’ of cryptocurrency investigations, walking through the practical aspects, and providing examples of tools, techniques, and resources that can be used for investigations.
No matter whether you are a counter fraud professional or are simply looking to understand how cryptocurrency investigations can be conducted, this blog will give you some very real insights.
Common Techniques Used by Investigators
Let’s start by discussing the techniques that form the backbone of cryptocurrency investigations. These span from the most basic blockchain analysis to more advanced techniques.
Transaction Tracing – ‘Following the Money’
The foundation of any cryptocurrency investigation is to ‘follow the money’. This is the concept of tracking the movement of funds, which we apply to the blockchain through transaction tracing.
Investigators can use blockchain explorers to start performing basic transaction tracing. These explorers provide near real-time logs, derived directly from the blockchain, for a given cryptocurrency address. By inputting a specific address or transaction hash (a unique identifier for a given transaction) into a blockchain explorer, investigators can:
- View all incoming and outgoing transactions for that address.
- Identify the amounts and timestamps of each transaction.
- Begin to track the path of funds across multiple addresses and transactions.
- Begin to spot patterns in transaction behaviour, such as frequent transactions with specific addresses.
- Begin to spot any further obfuscation techniques used by criminals, such as transaction peeling – where criminals split funds into smaller transactions, in the hope of avoiding detections.
walletexplorer.com – one of many blockchain explorer services
Now you may have picked up on the use of ‘begin to’ above. That’s because whilst these explorers provide the functionality to trace transactions, identifying any meaningful transaction flows or patterns using these explorers alone will be extremely time-consuming and sometimes impossible.
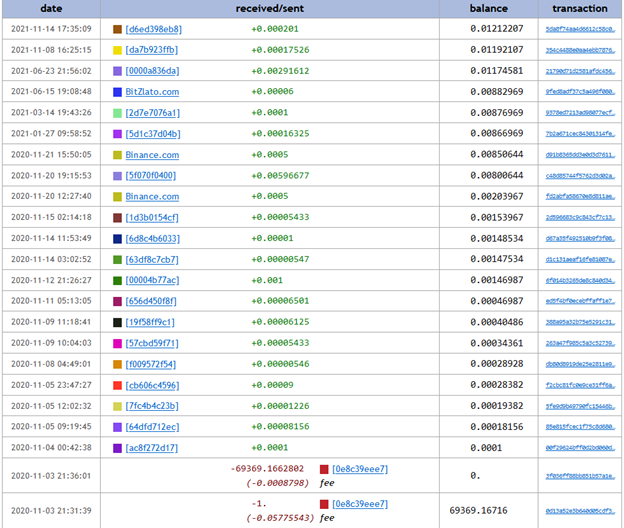
Example output from walletexplorer.com
This is where visualization tooling often comes into play. Tools like Breadcrumbs can help investigators visualize the flow of money as it interacts with known entities of interest on the blockchain, such as the crypto exchanges used for cashing out the proceeds.
The example below is a sample Breadcrumbs investigation of cryptocurrency transactions related to the Hydra Dark Web Market. We can see that some of the cryptocurrency that passed through Hydra’s address was sent to localbitcoins.com, a peer-to-peer cryptocurrency exchange made famous by even allowing users to utilize in-person cash trades for cryptocurrency.
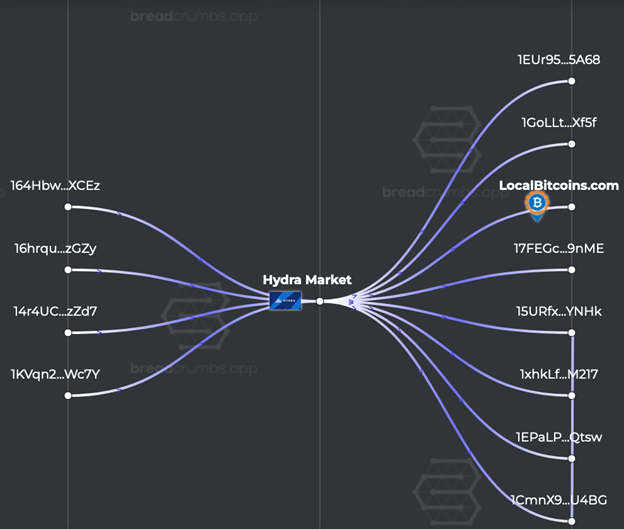
Sample Breadcrumbs Investigation
Another tool that can be used to achieve this is Maltego. The example below is one from Maltego’s blog, showcasing the logical flow of an address and the Binance crypto exchange. Both examples could be used to reveal points where identification and/or some fund recovery would most likely be possible.
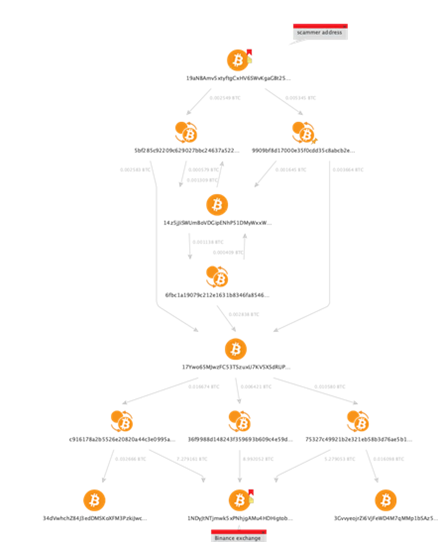
Example Maltego Investigation
Ethereum Contract Impersonation
For Ethereum addresses, a unique technique allows you to interact with decentralized applications (dApps) by impersonating a login from the address. This means you can spoof access to dApps as if logged in as the address owner, and while you can’t send or receive funds due to private keys, you can view the app from the address owners’ perspective. Tools like Impersonator enable this. For example, let’s impersonate Vitalik’s, founder of Ethereum’s connection on Uniswap.
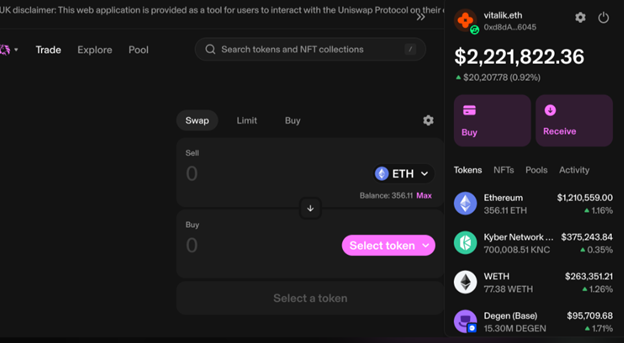
Vitalik.eth UniSwap Impersonation
From this you can see everything the address owns, the recent activity, the non-fungible tokens (NFTs), along with any hidden tokens assigned to their address.
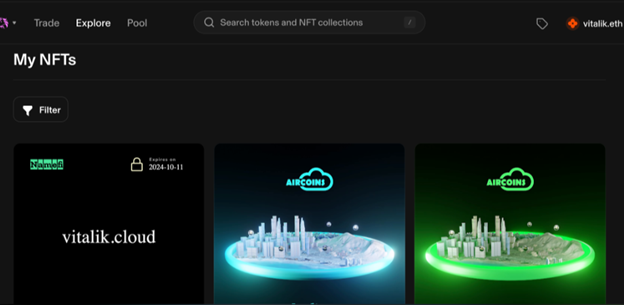
Vitalik.eth NFTs
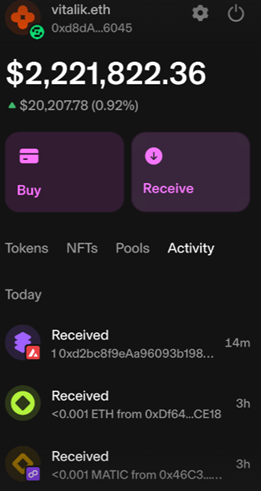
Vitalik.eth recent activity
This brings together key investigative data in a visual format, saving time compared to collating using blockchain explorers alone.
Address Clustering
Transaction tracing is crucial in the initial stages of an investigation and can sometimes obtain results on its own. However, if the criminal’s use of cryptocurrency is sophisticated, transaction tracing is often just a starting point. Next, investigators might start to use address clustering techniques to identify and group addresses likely to be controlled by the same entity. If individual criminals, or criminal groups are using multiple addresses to obscure their operations, clustering can help understand the full scope of their activities.
Explaining the exact theory and methods behind this could be a whole blog on its own, but here’s a high-level overview:
- Behavioral Analysis: Any addresses that are seen to be exhibiting similar patterns in frequency, amounts, timing are grouped.
- Common Inputs: If multiple addresses send money in a single transaction, they may belong to the same individual or group.
- Multi-Signature Wallets: Addresses that are frequently used together in transactions that require multiple approvals before being sent, are likely related.
Address Tagging and Attribution
An important part of clustering, and ‘following the money’ is having the ability to identify or tag addresses with known entities, particularly cryptocurrency exchanges. But you might be thinking, “how do sources and/or tools claim to identify exchange addresses with confidence?” This involves:
- Withdrawal/Deposit tracking: Investigators can make traceable deposits and withdrawals to build up a directory of known exchange wallets.
- Public Information and User Reports: Known exchange addresses may inadvertently be revealed by exchanges themselves or reported by their users.
- Fingerprinting Techniques: Using known addresses, some tools can fingerprint a transaction that may belong to a certain service. An example is if a certain exchange uses a very specific CoinJoin process to anonymize their Bitcoin for customers, this could give their transactions away.
Cross-Chain Analysis: Following the Money across Blockchains
As criminals increasingly move funds between different cryptocurrencies to further obscure transactions, cross-chain analysis becomes crucial for tracing funds and identifying conversion points between blockchains. This process builds on entity tagging and address clustering techniques, allowing investigators to link activities on different blockchains to the same entity. It involves monitoring exchange activity, analyzing cross-chain bridges, and applying inter-blockchain heuristics to connect transactions as they move across different blockchains.
Open-Source Intelligence
Now, whilst all the techniques we have discussed are important in analyzing blockchain data, Open-Source Intelligence (OSINT) can further enrich investigations. Let’s explore some of the key OSINT techniques using the well-documented Silk Road Marketplace address to provide examples:
Silk Road Marketplace – 1HQ3Go3ggs8pFnXuHVHRytPCq5fGG8Hbhx
Google Dorks
Using advanced Google search operators to find specific information, some useful examples being:
- Site:site.com intext:“1HQ3Go3ggs8pFnXuHVHRytPCq5fGG8Hbhx” – reveal any mentions of this address on your specific search site.
- (site:x.com OR site:facebook.com OR site:reddit.com OR site:pastebin.com) intext:” 1HQ3Go3ggs8pFnXuHVHRytPCq5fGG8Hbhx ” – reveal any mentions on common social media and discussion forum sites.
- (site:telegramchannels.me OR site:tlgrm.eu OR site:combot.org OR site:teleteg.com) intext:” 1HQ3Go3ggs8pFnXuHVHRytPCq5fGG8Hbhx ” – query Telegram search aggregators to reveal any indexed results. You can also use the Telegogo custom Google search engine, but you cannot query this with a dork.
- (site:github.com OR site:gitlab.com OR site:bitbucket.org OR site:sourceforge.net OR site:gitee.com OR site:code.google.com) intext:” 1HQ3Go3ggs8pFnXuHVHRytPCq5fGG8Hbhx ” – search any public code repositories for results.
- (site:ahmia.fi OR site:onionland.io OR site:oniongate.com) intext:” 1HQ3Go3ggs8pFnXuHVHRytPCq5fGG8Hbhx” – query Dark web search engines to reveal any indexed results. There are other dark web search engines available, but use any and all of these with extreme care.
Internet Archives
For historical lookups, the Wayback Machine or Archive.today allows investigators to check archived versions of websites that might have mentioned an address but have since been removed. We can see the results for the Silk Road address below.
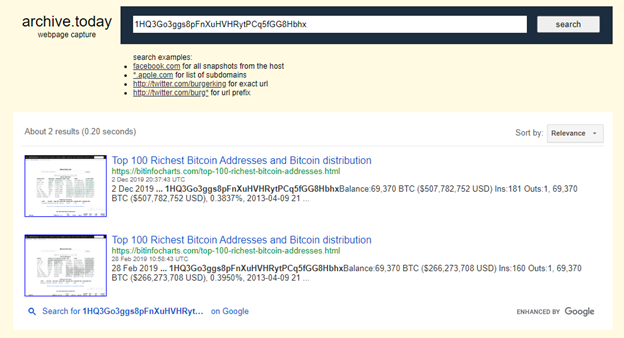
Results from Archive.today
Cryptocurrency Abuse Databases
We can also check an address’s reputation to see whether it has been previously reported. For this, we can use sites like BitcoinWhosWho or Chainabuse.
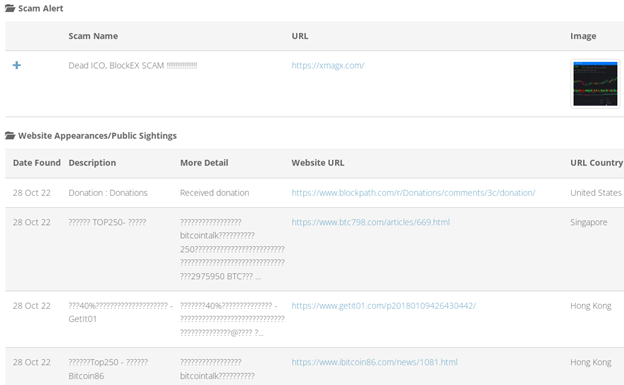
BitcoinWhosWhos Results
Bringing Everything to Life
While understanding these more advanced cryptocurrency investigative techniques – clustering, tagging, cross-chain analysis and OSINT to supplement investigations are hugely important, applying these is where the real challenges lie.
Commercial Offerings
To meet these needs, there are a range of solutions, both commercial and open source. The commercial market offers more feature-rich tooling designed for professional investigators. We aren’t here to review or recommend any specific tool, but some of the standouts are Chainanalysis, Elliptic, TRM Labs and Maltego CipherTrace.
When deciding upon commercial or open-source solutions, there are some important considerations:
- Cost vs. need: Evaluate if the outlay to obtain these tools matches your investigation scope and complexity. Consider both current and potential future investigations.
- Free-tier options: Some of these tools may offer feature-limited, or time restricted trials to test the tools. Determine if this will meet your investigation requirements.
- Licensing models: Confirm that your intended use is permitted by any licensing or usage restrictions for the tool. This applies for both commercial and open-source tooling.
- Learning curve: Consider the time needed to learn and get the most out of these tools.
Open-Source Offerings
While powerful, some commercial tools may be overkill for certain cases. It’s important to carefully assess your requirements and resources (more on this later). The good news is that open-source alternatives can bring together sophisticated capabilities at no cost. One such tool being GraphSense – a cryptocurrency analytics platform that offers a dashboard for interactive investigations.
GraphSense Maltego
Now GraphSense is a great tool on its own, but what if we could combine the power of Maltego with GraphSense? Well… that’s exactly what led the Interpol Innovation Center to create a bridging feature capable of performing “simple queries on GraphSense data and tag-packs to obtain transaction graphs and attribution tags in Maltego”.
This allows investigators to maximize the potential of Maltego for building a strong profile of the investigative case, inclusive of various entities, data points, blockchain-related data, and adversary data if known, whilst being able to easily perform cryptocurrency wallet attribution and clustering through GraphSense.
Below is an example of the types of investigations you can begin to undertake using this.
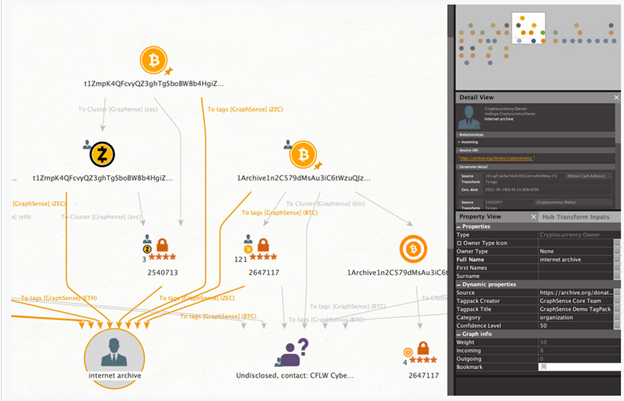
Interpol GraphSense Maltego plugin example investigation
Setting up a Cryptocurrency Investigation
It would be irresponsible to discuss this topic without first addressing the essential processes that fraud teams should have in place to initiate investigations. We have compiled this checklist to help you get started.
Before Investigations Start
Gain a foundational understanding of cryptocurrency:
- Understand the basics of blockchain technology and cryptocurrencies.
- Understand the key concepts such as wallets, addresses, exchanges, transactions.
- Understand the different types of wallets (hot and cold), public/private keys.
- Familiarize yourself with different types of cryptocurrencies and their unique features.
- Familiarize yourself with investigation techniques discussed in this blog.
Understand the legal, regulatory and compliance landscape:
- Consult with your legal counsel to understand the legal and regulatory implications of cryptocurrency investigations.
- Understand AML/KYC requirements and how these apply to cryptocurrency transactions.
- Understand evidentiary collection and maintaining procedures such as the Chain of Custody.
- Consider designating a responsible individual to review ongoing regulation and report back on any major relevant regulation changes.
Develop policies and procedures:
- Create internal policies for conducting cryptocurrency investigations in a manner that complies with all relevant laws and regulations.
- Establish Standard Operating Procedures (SOPs) for handling cryptocurrency investigations. These must include guidelines on data collection, evidence handling, and reporting points out to relevant agencies.
Before Each Investigation
Define investigation objectives:
- Clarify the specific goals of the investigation (e.g., identifying fraudsters, disrupting their activities, recovery of funds, preventing future fraud etc.).
- Determine what the success criteria of the investigation would be. This might also include key performance indicators (KPIs) for the investigation.
Define the investigation scope and identify resource requirements:
- Identify the scope, for example: Is it a single actor, or part of a larger fraud scheme?
- Identify necessary resources (personnel, tools, timing)
- Set boundaries so that the investigation is run efficiently and focused.
Risk assessments and internal approval:
- Conduct a risk assessment based on the investigation’s objectives, scope and resource requirements.
- Obtain necessary approvals from senior management and legal departments if investigation is determined to be high risk or deviates from the agreed SOPs.
Further Reading and Resources
Lastly, the community of individuals conducting cryptocurrency investigations are very collaborative and maintain a wealth of resources that will be helpful in enhancing your capabilities. Here’s some useful resources that should set you on your way.
- Law Enforcement Crypto Field Guide: a guide created by Chainanlysis, which provides some of the useful must-know elements to understand cryptocurrencies.
- Awesome On-Chain Investigations Handbook 2.0: a list of resources that can be used for various elements within an investigation, this is maintained by OfficerCia.
- Blockchain Dark Forest Self-Guard Handbook: which provides the context of Operational Security in cryptocurrency, this is maintained by the SlowMist Team.
- Crypto OpSec Self-Guard RoadMap: Collection and discussion about the best DeFi, Blockchain and crypto-related OpSec research, this project again is upheld by OfficerCia.
- Awesome OSINT Blockchain Analysis: a list of useful resources for OSINT investigations on cryptocurrency. This project is maintained by aaarghh on Github.


